The authorization happens when a user requests an action to an application before actually executing the action. You check by the access control rules that hold whether this user should be permitted to do this action. As we have dipped our feet in authentication and session management, let's dip more into authorization too as part of learning access control in web application. As we have covered some authentication and session management in previous blog posts, let's look more into authorization.
One of the most crucial aspects of authorization in web applications is deciding whether a request is legitimate. Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application whose authentication is currently valid. If the victim is a regular user, a successful CSRF attack can force the user to perform state-changing requests like transferring funds, changing their email address, etc. If the targeted victim is an administrative account, CSRF can compromise the entire web application. The picture below shows an example of a CSRF attack.
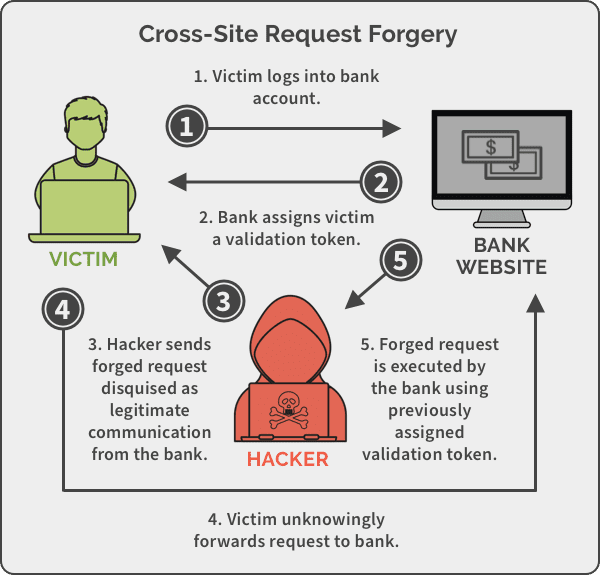
Nowadays, successfully finding and exploiting CSRF vulnerabilities often involves bypassing anti-CSRF measures deployed by the target website, the victim's browser, or both. Applications should verify if HTTP requests are legitimately generated via the application's user interface to prevent CSRF attacks. The best way to achieve this is through a CSRF token. A CSRF token is a unique, secret, and unpredictable value generated by the server-side application and shared with the client. When attempting a sensitive action, such as submitting a form, the client must include the correct CSRF token in the request. It makes it very difficult for an attacker to construct a valid request on behalf of the victim.
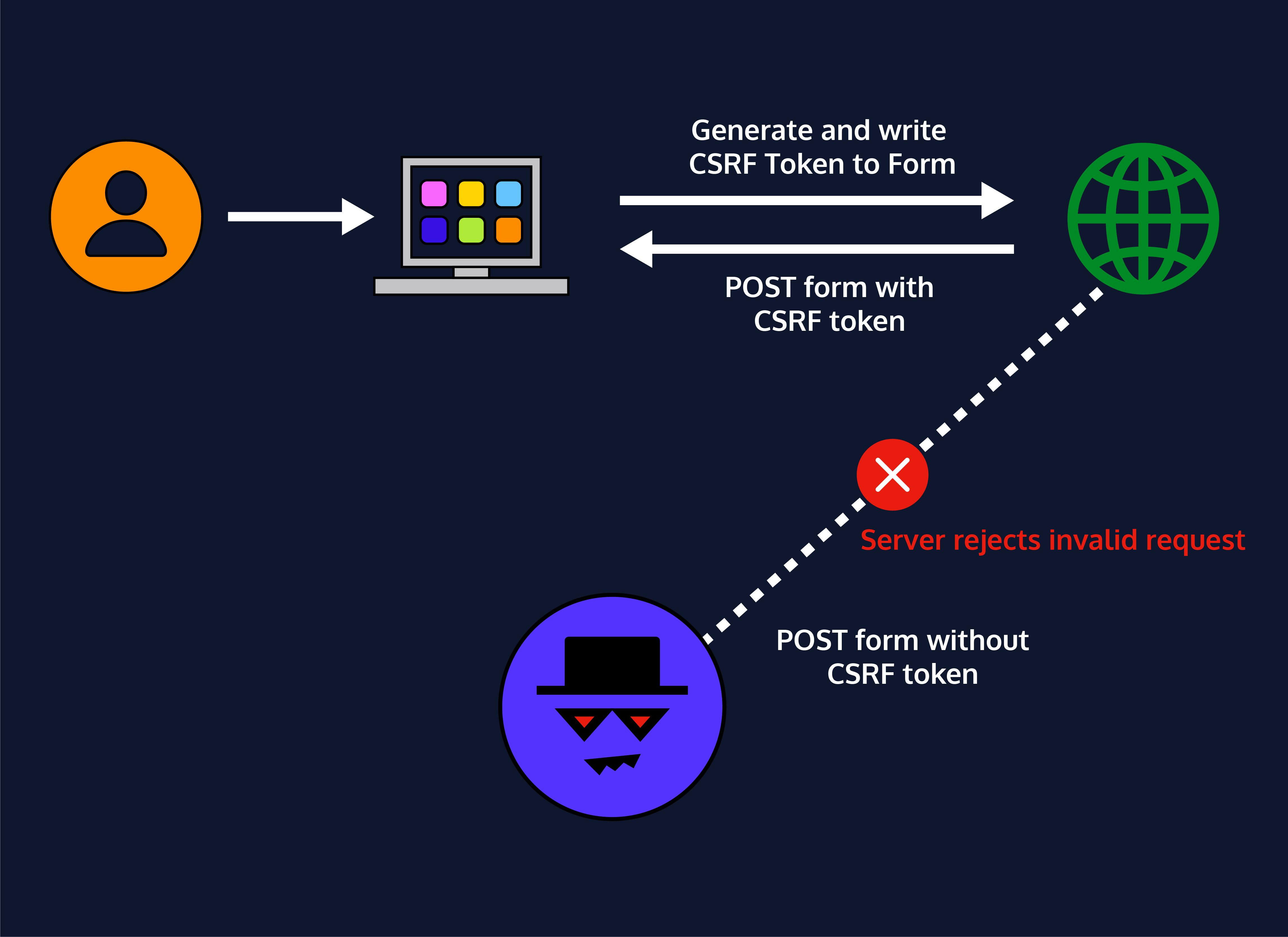
Another way to prevent CSRF attacks is using SameSite cookies. We have seen this cookie in our previous blogs. As requests to perform sensitive actions typically require an authenticated session cookie, the appropriate SameSite restrictions may prevent an attacker from triggering these actions cross-site. Some applications use the HTTP Referer header to defend against CSRF attacks by verifying that the request originated from the application's domain. It is generally less effective than CSRF token validation.
In conclusion, don't underestimate the importance of access control to the security of your application. When you design and develop your application, think about the application thoroughly. Think about what type of data you want to protect and which type of users you have. But to implement it, know that you are not the first one who has to tackle this problem. Don't start from scratch, but build on the primitives that coding frameworks these days give you.
